
Hackers are pirating online shops to show contemporary, realistic-looking phony payment types to take charge card from unwary consumers.
These payment types are revealed as a modal, HTML material overlayed on top of the primary web page, enabling the user to engage with login types or alert material without leaving the page.
When modals are active, the background material is often dimmed or blurred to accentuate the modal material.
In a brand-new report by Malwarebytes, MageCart skimmers are now pirating genuine online shop’s payment pages to reveal their own phony payment types as modals to take consumers’ charge card.
These modals stand apart due to the fact that they often look even much better than the initial, having no visual indications that might trigger suspicion that they are not genuine.
Much better than the genuine thing
One case highlighted in Malwarebytes’ report worries a PrestaShop-based Parisian travel device shop jeopardized by the brand-new Kritec project.
Kritec is a JavaScript charge card skimmer that Malwarebytes very first discovered on Magento shops in March 2022, so the exact same danger star is most likely behind it.
Malwarebytes reports that the skimmer that contaminated the page is rather complicated, and its code is greatly obfuscated with base64 encoding.
Upon reaching the checkout page of the contaminated website, rather of being revealed the website’s payment type, the harmful script shows a modal that includes the brand name’s logo design, proper language (French), and stylish user interface components.
Nevertheless, this phony payment type is developed to take consumers’ charge card info and send it back to the hackers.
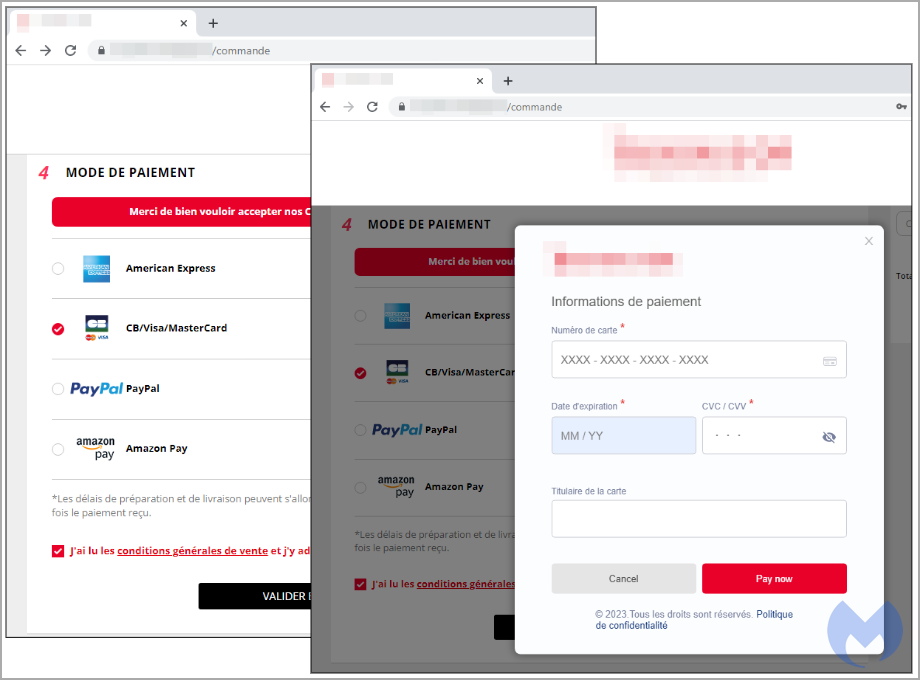
Once the purchasers enter their information on the modal, it shows a fake loader for a short time and after that reveals a phony mistake, rerouting the user to the genuine payment URL.
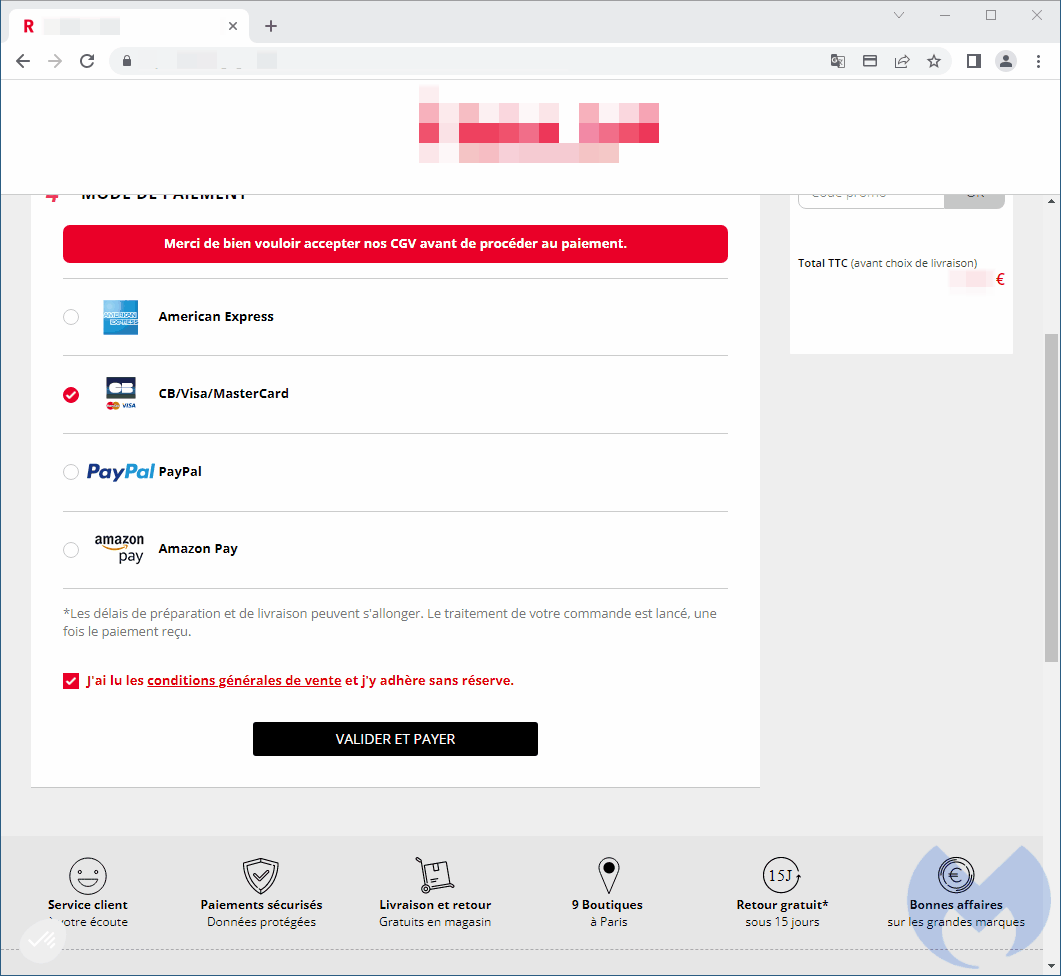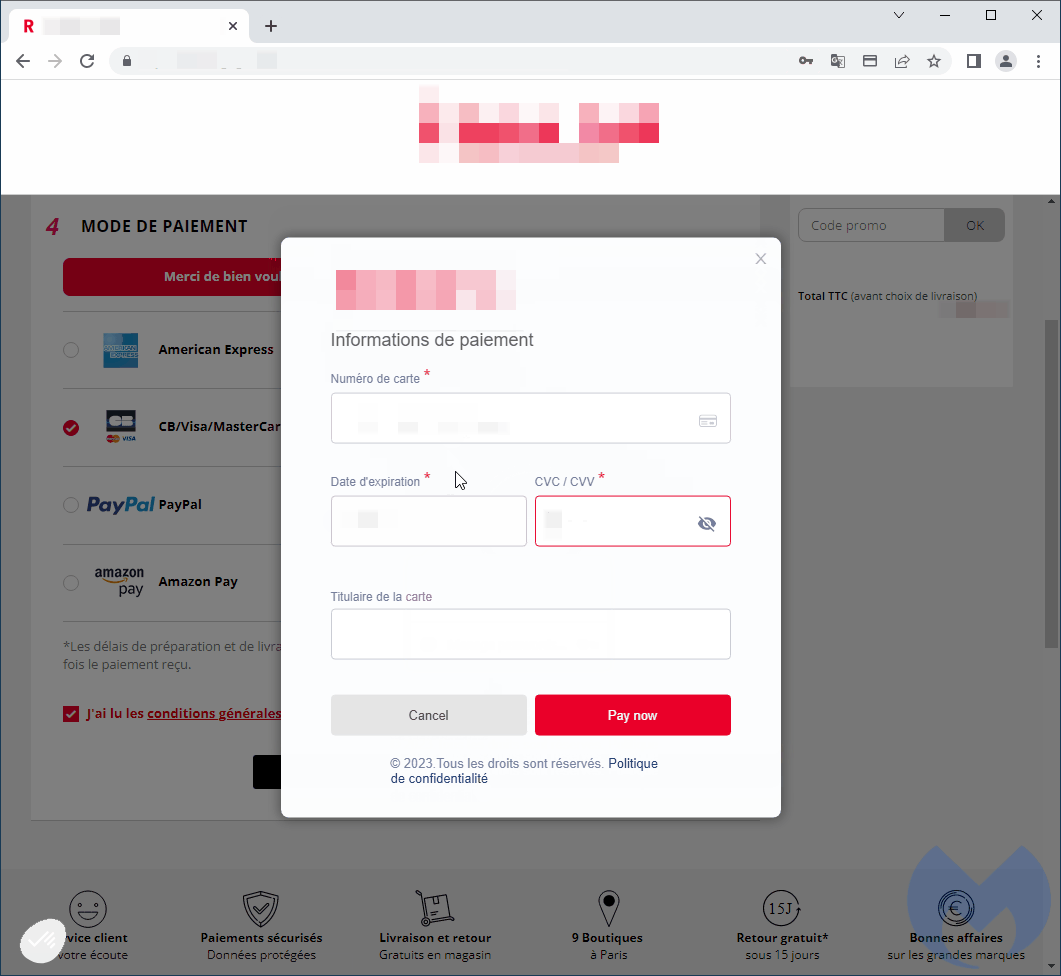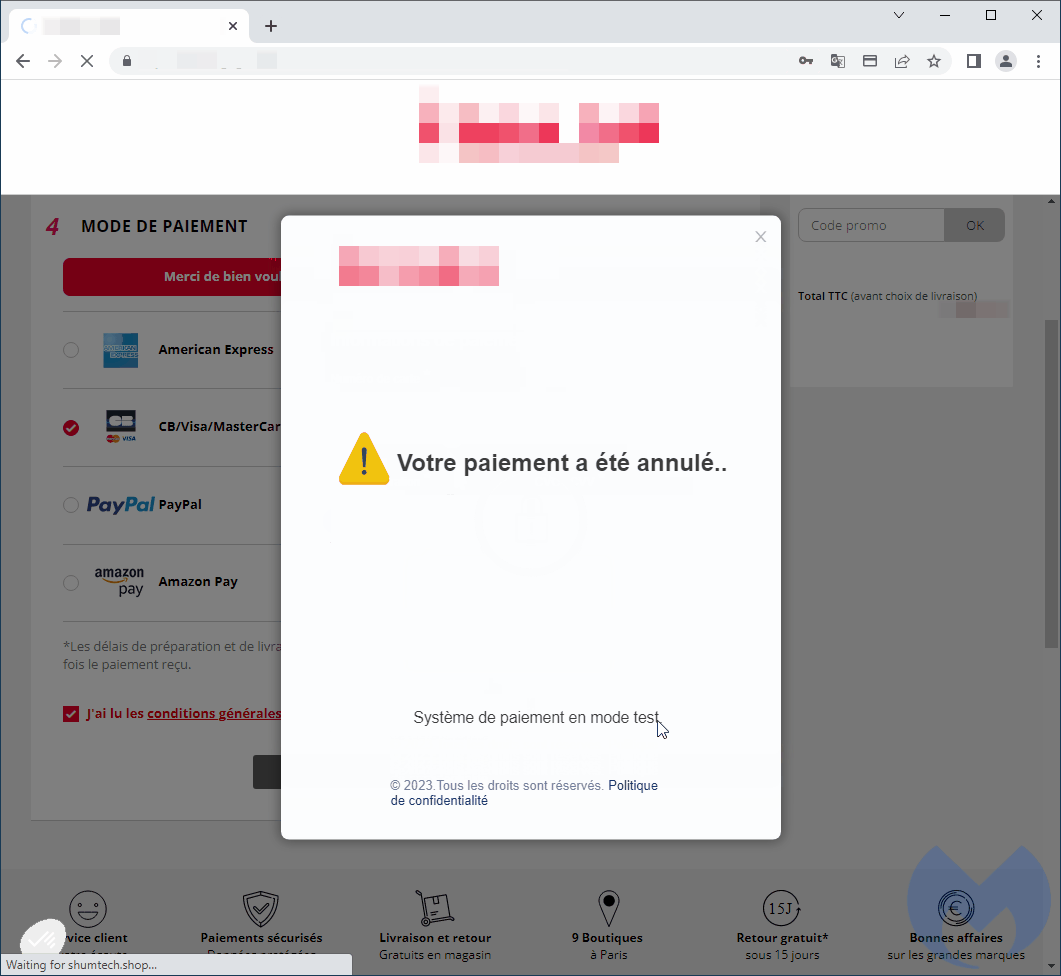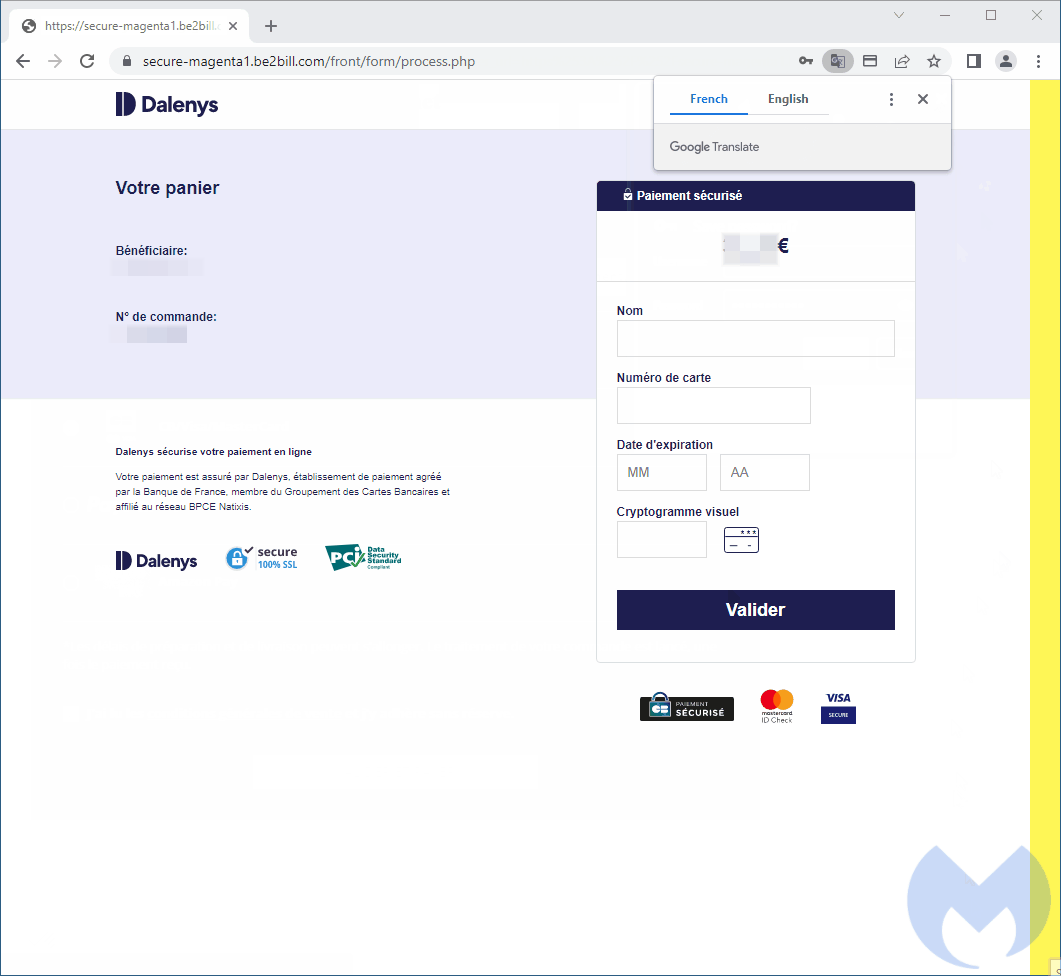
Nevertheless, in the background, the danger stars have actually currently taken all went into information, consisting of the charge card number, expiration date, CVV number, and cardholder name.
Likewise, the skimmer drops a cookie on users who have actually been effectively targeted to avoid packing the harmful modal once again on the exact same or another website. This is to prevent gathering replicate information and reduce the operation’s direct exposure.
Malwarebytes’ experts obstructed the charge card skimmer script to enable the initial payment type to load, and the contrast in between the 2 leaves the genuine one visually beat.
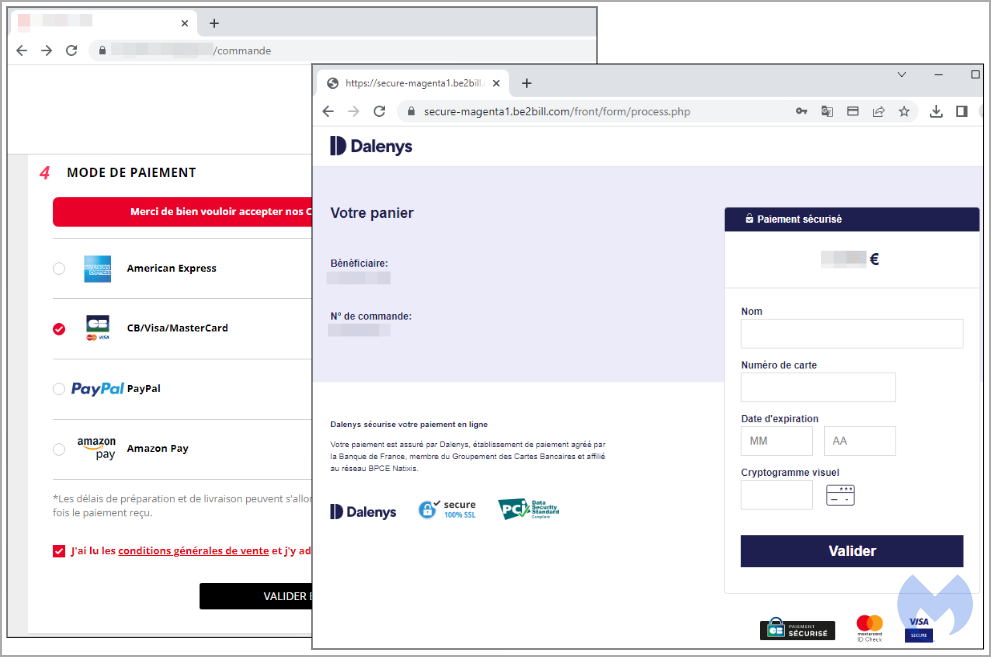
The real payment page reroutes visitors to a third-party processor, and after the banking info is gone into, the consumer go back to the store’s page.
While a redirection to an external website is a common action in online payments, it influences less rely on the visitor than the modal type rendered right on the page.
Regrettably, Malwarebytes observed proof that the pattern of utilizing modal types is acquiring traction in the Magecart cybercrime neighborhood.
Other examples of sites serving phony payment modals on visitors consist of a Dutch and a Finnish e-commerce website, both including stylish style that assists them pass as genuine.
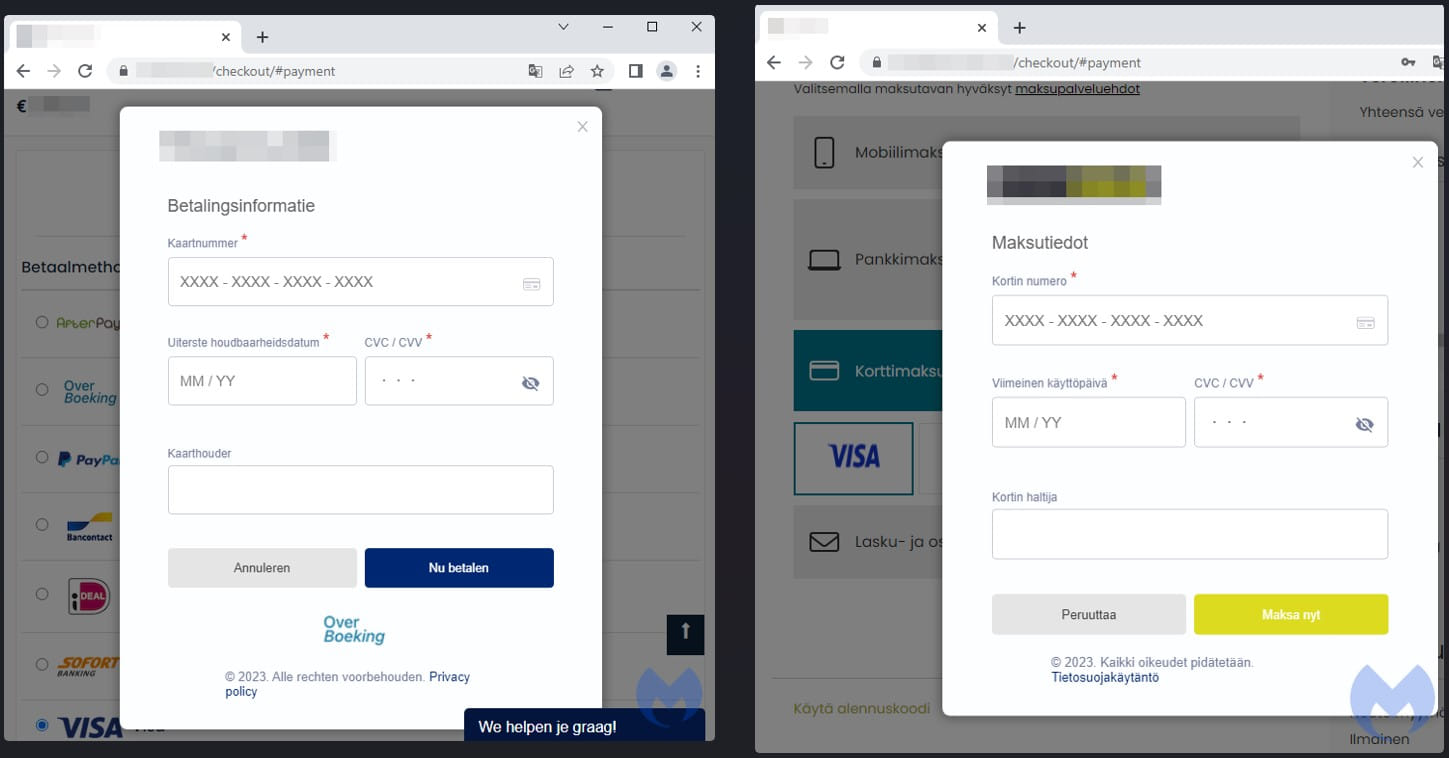
” It is possible numerous danger stars are associated with those projects and personalizing skimmers appropriately,” checks out the report
” While lots of hacked shops had a generic skimmer, it appears the custom-made modals were established relatively just recently, possibly a month or more earlier.”
Online consumers require to be extremely watchful and choose electronic payment techniques or one-time personal cards with charge limitations that are worthless in the hands of cybercriminals.