
Phony extortionists are piggybacking on information breaches and ransomware events, threatening U.S. business with publishing or offering presumably taken information unless they make money.
In some cases the stars include the threat of a dispersed denial-of-service (DDoS) attack if the message recipient does not adhere to the guidelines in the message.
Bad stars
The assaulters behind this activity utilize the name Midnight and began targeting business in the U.S. considering that a minimum of March 16.
They have actually likewise impersonated some ransomware and information extortion gangs in e-mails and declared to be the authors of the invasion, taking numerous gigabytes of essential information.
In one e-mail to the staff member of a holding business in the market of petroleum ingredients, the danger star declared to be the Quiet Ransom Group ( SRG) – a splinter of the Conti distribute concentrated on taking information and obtaining the victim, likewise referred to as Luna Moth
The very same message, nevertheless, utilized in the subject line the name of another danger star, the Surtr ransomware group, initially seen to secure business networks in December 2021.

source: BleepingComputer
BleepingComputer discovered another e-mail from Midnight Group, proclaiming that they were the authors of the information breach which they took 600GB of “vital information” from the servers.
The messages were sent out to the address of a senior monetary coordinator that had actually left the target business over half a year prior to.
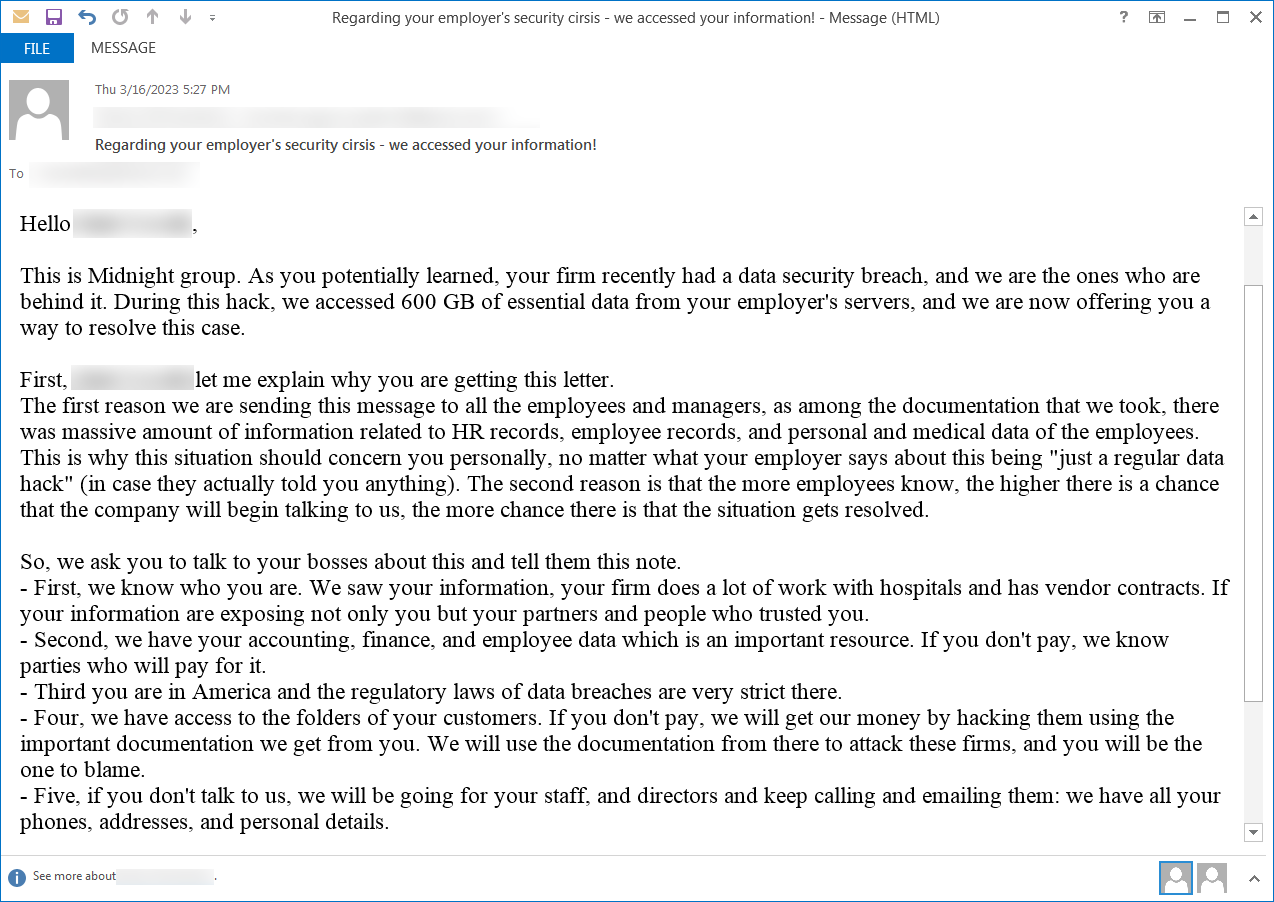
source: BleepingComputer
Pending DDoS danger
A report in late March from the handled detection and reaction department at the Kroll business examination and danger consulting company keeps in mind that some senders of comparable e-mails likewise threatened with DDoS attacks.
Kroll detectives state that beginning March 23 companies began submitting an increased variety of reports for e-mails gotten under the Quiet Ransom Group name.
It’s “a new age of phony extorsion efforts,” Kroll responders state in the report, including that the authors utilize the names of better-known cybercriminals in an effort to frighten and offer authenticity to the danger.
” This approach is inexpensive and quickly carried out by low-skilled assaulters. Just like 419 wirefraud frauds, the fraud counts on social engineering to obtain victims by positioning pressure on the victim to pay prior to a due date. We anticipate this pattern to continue forever due to its expense efficiency and capability to continue to produce profits for cybercriminals” – Kroll
Kroll has actually seen such events considering that 2021, although such activity began in early November 2019, when non-paying victims likewise experienced DDoS attacks.
However, the attacks were low-level DDoS and included the danger of bigger ones unless the extortionists earned money.
Such events echo the activity of an extortion group that in 2017 sent out DDoS risks to countless business under the names of notorious hacker groups at the time (e.g. New World Hackers, Lizard Team, LulzSec, Fancy Bear, and Confidential).
Targeting ransomware attack victims
Another report from occurrence reaction business Arete validates Kroll’s observations about Midnight Group’s deceitful e-mails impersonating Surtr and SRG and the bigger variety of messages provided in the weeks prior to March 24.
Based upon their exposure, however, the occurrence responders observed that Midnight targeted companies that had actually formerly been victims of a ransomware attack.
According to Arete’s experts, amongst the preliminary assaulters are QuantumLocker (presently rebranded as DagonLocker), Black Basta, and Luna Moth.
Arete states that a minimum of 15 of their present and previous customers got phony risks from the Midnight Group, which supported their information theft declares with unclear information.
It is uncertain how victims are chosen however one possibility is from openly readily available sources, such as the preliminary opponent’s information leakage website, social networks, report, or business disclosures.
Nevertheless, Arete keeps in mind that the phony opponent determined some ransomware victims even when the details was not openly readily available, perhaps showing cooperation with the preliminary trespassers.
Ransomware stars frequently offer the information they take from victims even when they make money. If Midnight Group has access to the marketplaces and online forums where this information is traded or offered they might discover ransomware victims that have yet to reveal the cyberattack.
Empty risks considering that 2019
Midnight Group’s extortion fraud is not brand-new. The technique has actually been observed in 2019 by ransomware occurrence reaction business Coveware who calls it Phantom Occurrence Extortion
Coveware describes that the danger star attempts to offer trustworthiness to the danger by utilizing information that is special to the recipient target, includes the pressure of an expensive result, and needs payment that is far less than the damage of public direct exposure.
All these 3 parts are the essentials of a phantom occurrence extortion (PIE) and a clear sign of an empty danger.
Coveware at first supplied 4 examples of PIE frauds and upgraded the report just just recently with a sample e-mail from the Midnight Group.
All 3 business evaluate that Midnight Group’s risks belong to a scams project. Arete’s effort to engage with the star led to no reaction or proof of taken information from the star.
The suggestion is to thoroughly evaluate such e-mails to acknowledge the parts of a phantom occurrence extortion message and dismiss them as an empty danger.