Research study and advancement of quantum computer systems continues to grow at a fast rate. The U.S. federal government alone invested more than $800 million on quantum info science (QIS) research study in 2022. The pledge of quantum computer systems is significant– they will have the ability to resolve particular issues that are classically intractable, indicating a traditional computer system can not finish the computations within human-usable timescales. Provided this computational power, there is growing conversation surrounding the cyber dangers quantum computer systems might posture in the future. For example, Alejandro Mayorkas, secretary of the Department of Homeland Security, has actually determined the shift to post-quantum file encryption as a concern to guarantee cyber strength There is really little conversation, nevertheless, on how we will safeguard quantum computer systems in the future. If quantum computer systems are to end up being such important properties, it is sensible to forecast that they will become the target of harmful activity.
I was just recently welcomed to be an individual in the Workshop on Cybersecurity of Quantum Computing, co-sponsored by the National Science Structure (NSF) and the White Home Workplace of Science and Innovation Policy, where we took a look at the emerging field of cybersecurity for quantum computing. While quantum computer systems are still nascent in lots of methods, it is never ever prematurely to resolve looming cybersecurity issues. This post will check out problems connected to producing the discipline of cyber security of quantum computing and summary 6 locations of future research study in the field of quantum cybersecurity.
What is Quantum Computing?
The typical computer systems that many people utilize every day are developed on the binary reasoning of bits, which are based upon 0 and 1 as represented by a binary physical residential or commercial property, such as whether circulation of electrical energy to a transistor is off or on. These standard computer systems are generally described as classical computer systems when gone over in relation to quantum computer systems. In contrast to the binary nature of classical computer systems, quantum computer systems utilize qubits, which can remaining in a superposition of 2 states at the very same time (i.e., representing both a 0 and 1 at the very same time). One example to comprehending superposition is to think about turning a coin. A classical computer system can represent the coin as being heads or tails after the coin lands. A quantum computer system, on the other hand, can represent the coin as both heads and tails at the very same time while it is still turning in the air.
The ability of quantum computer systems is more enhanced by the residential or commercial property of entanglement, which allows dispersed encoding of info. Quantum entanglement permits qubits that are separated, even by substantial ranges, to engage with each other immediately. Entanglement takes place when particles engage in such a method that each particle’s quantum state can not be explained individually of the state of the others. That is, the determined states of knotted particles are associated such that measurement of state for a single particle allows probabilistic forecast of state for others. Think about the coin turning example from above; now envision that 2 coins are turned at the very same time. As they are turning in the air, the states of each coin are associated.
Jointly, quantum superposition and entanglement make it possible for significant computing power. Think about that a 2-bit register in a classical computer system can save just one of 4 binary mixes (00, 01, 10, or 11) at an offered time, however a 2-qubit register in a quantum computer system can save all 4 of these numbers concurrently. As more qubits are included, this computational benefit of quantum computer systems over classical computer systems grows significantly.
Cyber Hazards to Quantum Computers
The existing state of quantum computer system systems is typically described as the NISQ (loud intermediate-scale quantum) period, defined by quantum computer systems that use moderate calculating power and are still challenged by system fidelity. Existing quantum computer systems are unpredictable and unsteady, with error-correction for quantum computations still being dealt with. While scientists work to resolve these difficulties, it appears that in the near-term– and even more into the near-future– quantum computer systems will probably be utilized as co-processors in hybrid systems in which classical computer systems will hand off mathematical computations to the quantum computer system as part of a bigger system workflow that still greatly depends upon classical computer systems. The diagram listed below programs a notional idea of the parts for a quantum-classical hybrid comuting environment. Application information will differ by quantum architectures, however comparable layers will exist in all quantum-classical hybrid computer systems.
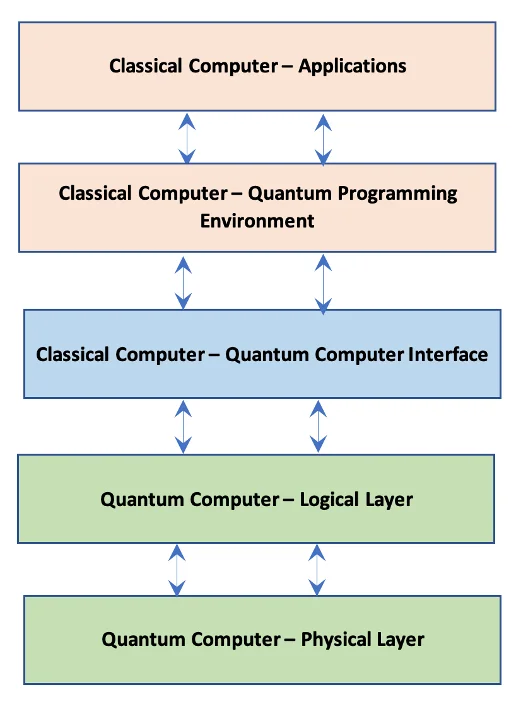
Figure 1: Notional Design of Classical-Quantum Hybrid Computer System.
Comprehending how quantum computer systems will be incorporated with classical computer systems is vital to thinking about the cyber dangers to quantum computer systems. The user interface in between classical and quantum computer systems in the hybrid computing environments normal of the NISQ-era is a location ripe for cybersecurity dangers. This user interface is actually the entrance in between the classical and quantum environments, so it can function as an avenue for recognized exploits of classical computer systems to pass through into quantum locations. Simply put, there are currently lots of recognized cyber attack strategies for classical computer systems that can be leveraged to jeopardize a hybrid system.
Another attack vector comes from unique methods for control and measurement of quantum gadgets that will be executed in these user interfaces. Application-specific incorporated circuits (ASICs), field-programmable gate ranges (FPGAs), digital-to-analogue converters (DACs), and other aspects of classical-quantum user interfaces are being utilized in brand-new methods. The existing focus of research study in developing these user interfaces is on performance and efficiency, yet security issues likewise should be dealt with. Provided the lots of recognized strategies for jeopardizing classical computer systems, it appears likely that attacks on quantum computer systems will come from weak points in classical computer systems and after that propagate to the quantum-classical user interface.
Research study sponsored by Microsoft Quantum Sydney details scalability problems connected to existing methods for classical-quantum user interfaces. The research study highlighted difficulties connected to I/O management, heat and power dissipation, system footprint, sound and disturbance, and bandwidth. While these problems exist in relation to scalability, the very same problems supply opportunities for attack. For example, enemies can take advantage of the heat level of sensitivity to make it possible for a denial-of-service attack or the predisposition for sound and disturbance to assault the stability of operations. Our operate in cybersecurity of classical computer systems has actually taught us that any system failure can supply an opening to make use of a system.
While protecting the classical-quantum user interface is an important component in quantum cybersecurity, there are other locations to resolve. For example, the output of quantum computing computations will be a lot more important to safeguard (and important to take) than the majority of classical computer system output, offered the resources needed to carry out the computations and obtain the output. For example, an industrial pharmaceutical business utilizing a quantum computer system to resolve an intricate chemistry issue will think about that output rather important since it might be tough to recreate and the end-product will containly extremely important copyright.
Additionally, the large computing power in quantum computer systems demands safeguarding the quantum computational power itself. That is, not simply safeguarding algorithms and their outputs however likewise finding and safeguarding versus hijacking of quantum computing ability, in the very same method a botnet attack pirates classical computing power. For instance, if foes do not have quantum computing power of their own, however wish to carry out a resource-intensive computation, then they might attempt to get unapproved access to somebody else’s quantum ability. Similarly, a foe might simply wish to interfere with quantum-based calculations exclusively to negatively affect the outcomes.
Finally, a crucial distinction in between quantum computer systems and classical computer systems is their level of sensitivity to temperature level and the real world in basic, which opens brand-new vectors for denial-of-service-attacks. For example, the refrigeration requirements for lots of quantum architectures opens an opportunity to carry out a denial-of-service attack: interfere with the cooling for these architectures and their whole operation can be stopped. These are the most important of the lots of dangers to quantum computer systems that the brand-new discipline of quantum cybersecurity should resolve.
6 Secret Locations of Future Research Study in Quantum Cybersecurity
Because the style and architecture of quantum computer systems is still an open location of research study with lots of options being checked out, it is early to concentrate on particular vulnerabilities in particular systems. Scientists in this field should initially form an understanding of existing and future dangers to quantum computer systems to establish more efficient securities. The preceding area highlighted different dangers to the privacy, stability, and accessibility of quantum computer systems. This area higlights locations of research study required to establish securities versus these dangers.
For instance, one crucial location for future research study is the advancement of abilities for keeping track of quantum calculations. Quantum processing can not be kept an eye on in the very same methods that system tracking is provided for classical computer systems, that makes it tough to both evaluate what algorithms quantum computer systems are running and figure out whether harmful processing is happening. This space shows the requirement for establishing a multi-layered instrumentation structure for quantum computer systems, which is among the following 6 crucial locations for future quantum security research study we determined in the Workshop on Cybersecurity of Quantum Computing:
- Structure safe massive control systems The scale of the classical calculation associated with supporting a massive quantum computer system can be comprehensive. This assistance consists of control systems and mistake correction, however it can likewise consist of keeping track of for invasions. Research study is required on structure safe classical control systems for quantum computer systems.
- Making it possible for dispersed high-performance quantum computing Classical high-performance computing systems are generally multi-tenant and dispersed. Resolving the security of multi-tenant and dispersed quantum computer systems now can lay the structure for more safe quantum computer systems when they attain scale.
- Comprehending attack vectors on various kinds of quantum computer systems Much deeper research study on prospective attack vectors for different quantum system designs, such as whether foes just gain access to quantum gadgets through an interface, is required to more completely comprehend how to protect quantum computer systems.
- Developing official approaches for safe and safe quantum computing systems In computing, official approaches describe strenuous mathematical strategies for defining, establishing, and confirming computer system software application and hardware. Research study is required on establishing official approaches for quantum computing to attain credible quantum computing.
- Building a multi-layered instrumentation structure Such a structure would enable security-relevant residential or commercial properties of quantum computer systems to be imposed or confirmed.
- Establishing the needed tools for company to confirm quantum algorithms. These tools will make it possible for the capability to confirm and manage which algorithms are operating on a quantum computer system, likewise assists guarantee that a quantum computer system will not carry out unfavorable habits.
While all these locations of research study are crucial for safeguarding quantum computer systems, the landscape of cyber dangers will constantly alter as quantum computing innovation develops. All the above locations need to be looked into and, in tandem, extra locations for quantum cybersecurity research study need to be included as they end up being appropriate. Methods for safeguarding classical computer systems, such as risk modeling and thinking about methods to jeopardize the concepts of the privacy, stability, accessibility (CIA) triad, should be used constantly to quantum computer systems to find emerging dangers to research study as this field of quantum cybersecurity advances.
Protecting Increased Quantum Implementation Conclusion
As quantum computing ends up being more useful, companies should address lots of concerns about how to take advantage of it for tactical usage. Increased quantum implementation will raise lots of technical concerns about how information is prepared and moved to quantum computer systems, how algorithms are executed in quantum computer systems, and how quantum computing outcomes are returned and confirmed. With all these technical factors to consider, an overarching concern will be, How can this all be done firmly? Here at the CERT Department of the SEI, we have a long history of safeguarding software application and computing systems. Additionally, when the time concerns make clever, safe choices about using quantum computer systems, we are all set to invite you to quantum cybersecurity!