As the volume, speed and range of information grows, companies are significantly depending on strong information governance practices to guarantee their core company results are effectively fulfilled. Unity Brochure is a fine-grained governance option for information and AI powering the Databricks Lakehouse. It assists streamline the security and governance of your business information possessions by offering a central system to administer and investigate information gain access to.
Taking a journey down memory lane, prior to Unity Brochure combined the authorization design for files, tables and included assistance for all languages, clients were executing fine-grained information gain access to control on Databricks utilizing the tradition workspace-level Table ACL (TACL), which were basically limited to specific cluster setups and worked just for Python & & SQL. Both Unity Brochure & & TACL let you manage access to securable things like brochures, schemas (databases), tables, views, however there are some subtleties in how each gain access to design works.
A mutual understanding of the things gain access to design is necessary for executing information governance at scale utilizing Unity Brochure. Much more so, if you have actually currently carried out the Table ACL design and are seeking to update to Unity Brochure to make the most of all the most recent functions, such as multi-language assistance, central gain access to control and information family tree
The Axioms of Unity Brochure gain access to design
- Unity Brochure opportunities are specified at metastore – Unity Brochure approvals constantly describe account-level identities, while TACL approvals specified within the hive_metastore brochure constantly describe the regional identities in the work space
- Advantage inheritance – Things in Unity Brochure are hierarchical and opportunities are acquired downward. The greatest level things that opportunities are acquired from is the brochure
- Object ownership is very important – Opportunities can just be given by a metastore admin, the owner of an item, or the owner of the brochure or schema which contains the things. Just the owner of an item, or the owner of the brochure or schema which contains it can drop the things
- usage opportunities for limits – USAGE CATALOG/SCHEMA is needed to communicate with things within a catalog/schema. Nevertheless, usage opportunity does not permit one to search the things metadata that is housed within the catalog/schema
- Consents on obtained things are streamlined – Unity Brochure just needs the owner of a view to have SELECT opportunity, in addition to usage SCHEMA on the views’ moms and dad schema and usage brochure on the moms and dad brochure. On the other hand with TACL, a view’s owner requires to be an owner of all referenced tables and views
Some more intricate axioms
- Secure by default – just clusters with Unity-Catalog particular gain access to modes (shared or single-user) can access Unity Brochure information. With TACL, all users have access to all information on non-shared clusters
- Restriction of single-user clusters – Single users clusters do not support vibrant views. Users need to have SELECT on all referenced tables and views to check out from a view
- No assistance for ANY FILE or Confidential FUNCTIONs: Unity Brochure does not support these approvals, as they might be utilized to prevent gain access to control constraints by permitting an unprivileged user to run fortunate code
Intriguing patterns
There are lots of governance patterns that can be attained utilizing the Unity Brochure gain access to design.
Example 1 – Constant approvals throughout work spaces
Axiom 1 permits item group to specify approvals for their information item within their own work space, and having actually those shown and imposed throughout all other work spaces, no matter where their customers are originating from
Example 2 – Setting limit for information sharing
Axiom 2 permits catalog/schema owners to establish default gain access to guidelines for their information. For instance the following commands allow the device finding out group to produce tables within a schema and check out each other’s tables:
PRODUCE brochure ml;
PRODUCE SCHEMA ml.sandbox;
GRANT USE_CATALOG ON brochure ml TO ml_users;
GRANT USE_SCHEMA ON SCHEMA ml.sandbox TO ml_users;
GRANT PRODUCE TABLE ON SCHEMA ml.sandbox TO ml_users;
GRANT SELECT ON SCHEMA ml.sandbox TO ml_users;More remarkably, axiom 4 now permits catalog/schema owners to restrict how far private schema and table owners can share information they produce. A table owner approving SELECT to another user does not permit that user checked out access to the table unless they likewise have actually been given usage brochure opportunities on its moms and dad brochure in addition to usage SCHEMA opportunities on its moms and dad schema.
In the listed below example, sample_catalog is owned by user A, user B produced a sample_schema schema, and table 42. Despite The Fact That Usage SCHEMA and SELECT authorization is given to the experts group, they still can not query the table, due to authorization limit set by user A
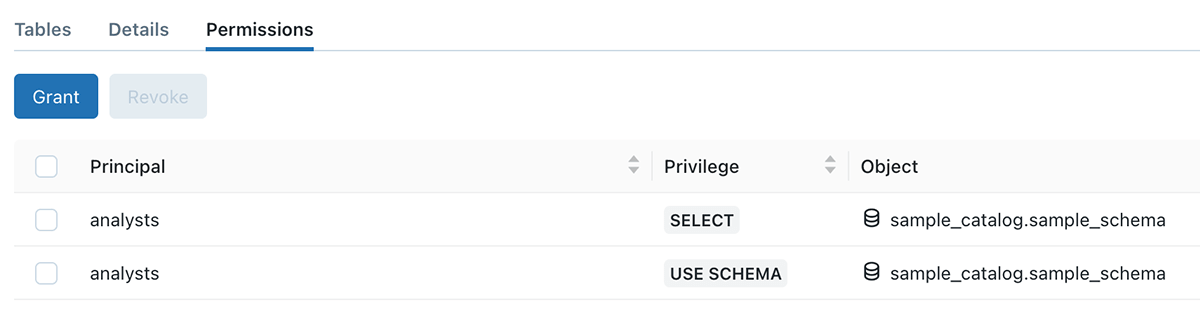
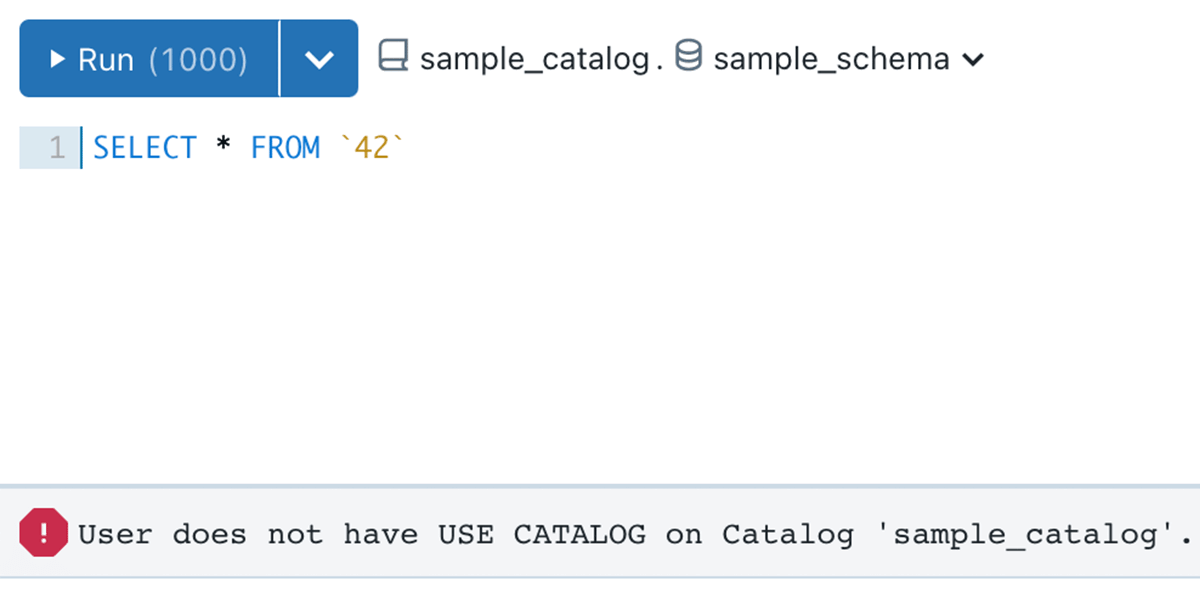
Example 3 – Simpler sharing of company reasoning
Information customers have a requirement to share their operations and change reasoning, and a multiple-use method of doing it is by developing and sharing views to other customers.
Axiom 5 opens the capability for information customers to do this effortlessly, without needing handbook backward and forward with the table owners.
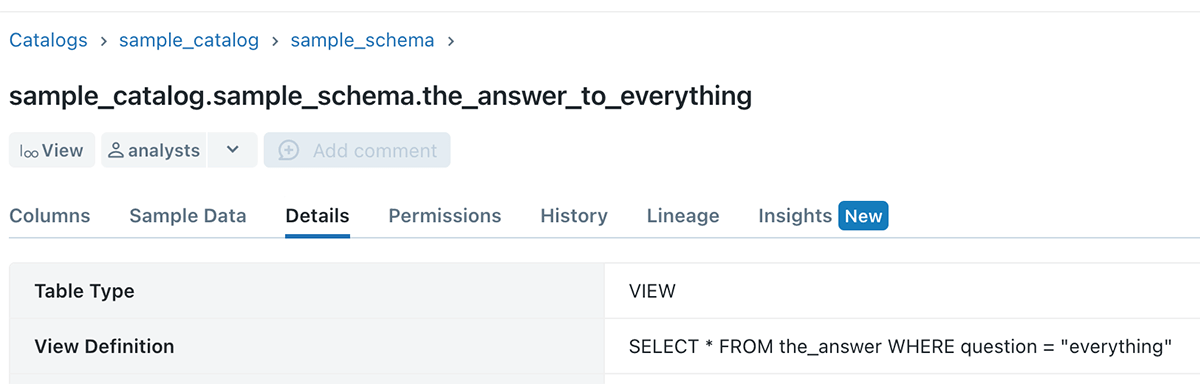
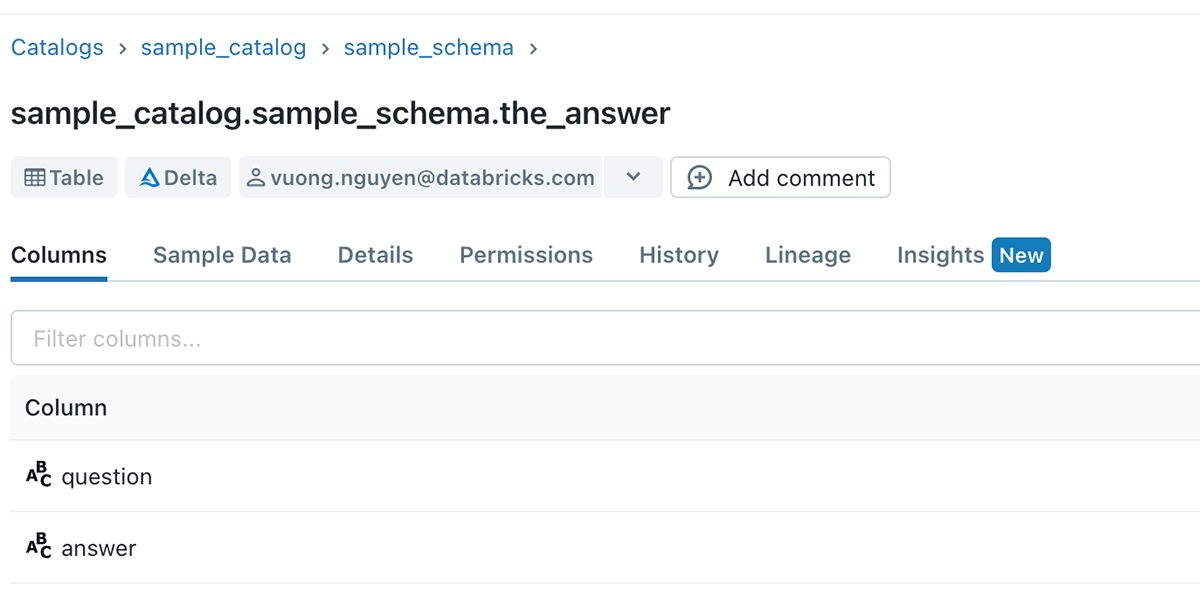
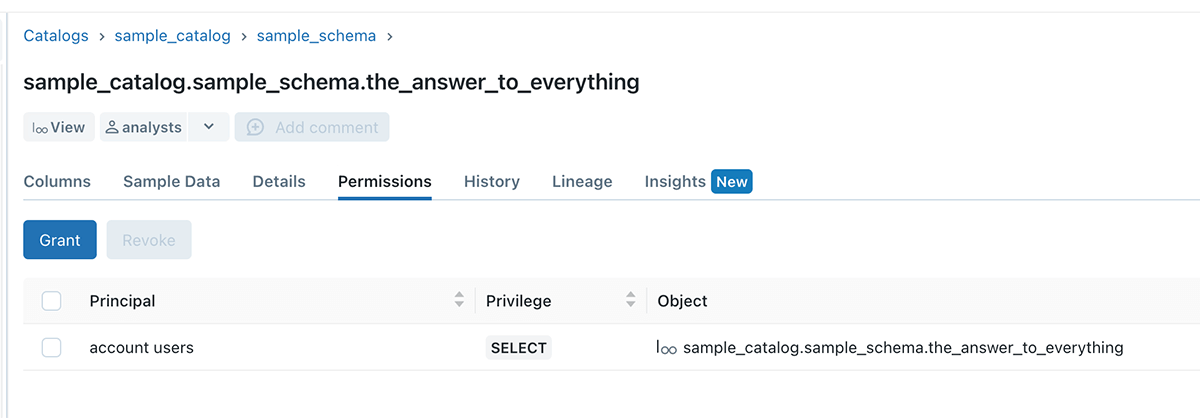
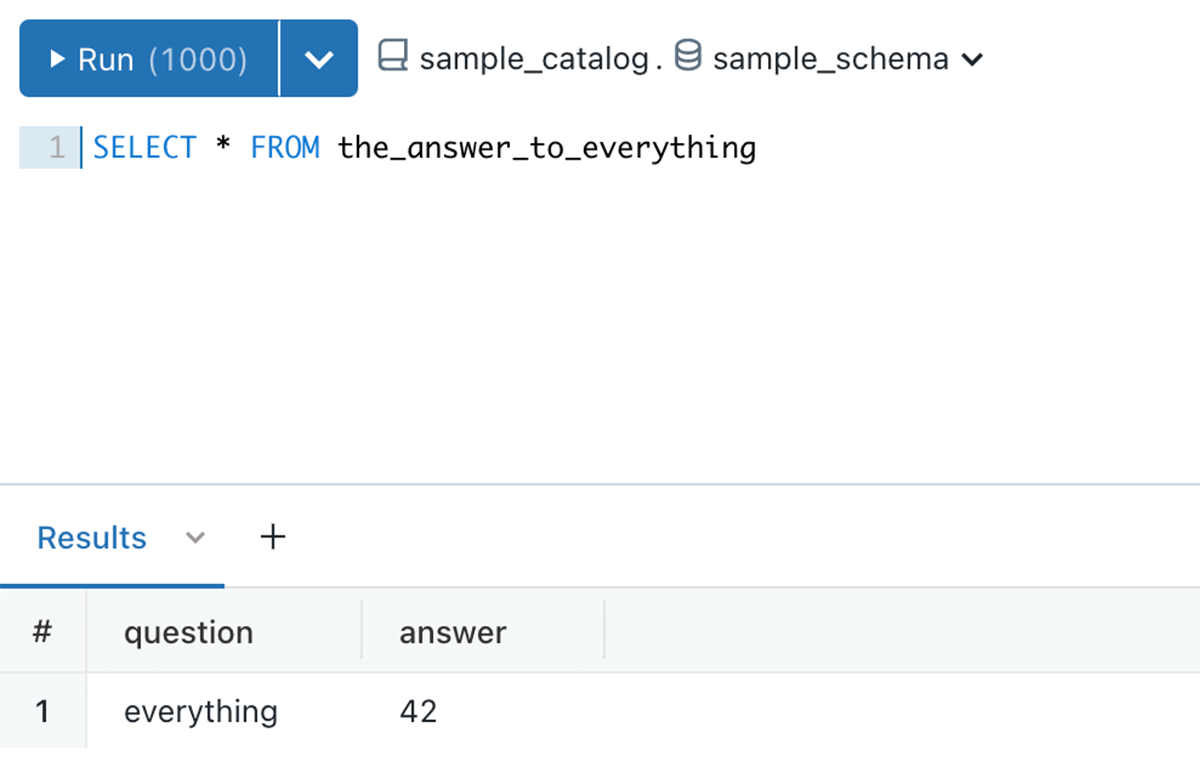
Example 4 – No more information leak
Thanks to axiom 6, information owners can be specific that there will be no unapproved access to their information due to cluster misconfiguration. Any cluster that is not set up with the appropriate gain access to mode will not have the ability to gain access to information in Unity Brochure.
Users can examine that their clusters can access Unity Brochure information thanks to this helpful tooltip on the Develop Clusters page
Now that information owners can comprehend the information opportunity design and gain access to control, they can utilize Unity Brochure to streamline gain access to policy management at scale.
There are upcoming functions that will even more empower information administrators and owners to author much more intricate gain access to policy:
- Row filtering and column masking: Usage basic SQL functions to specify row filters and column masks, permitting fine-grained gain access to controls on rows and columns.
- Quality Based Gain Access To Controls: Specify gain access to policies based upon tags (characteristics) of your information possessions.